Categories
WebSecurity
How I perform the JSON CSRF with method override technique.
CSRF(Cross-Site Request Forgery) is a kind of web application vulnerability, using this a malevolent can forge the HTTP request without the actual user knowledge. This will result in ...
In WebSecurity, APISecurity, Dec 29, 2023The Art of Identifying X$$ & WAF Bypass Fuzzing Technique.
A smart way to hunt Cross-Site Scripting vulnerability
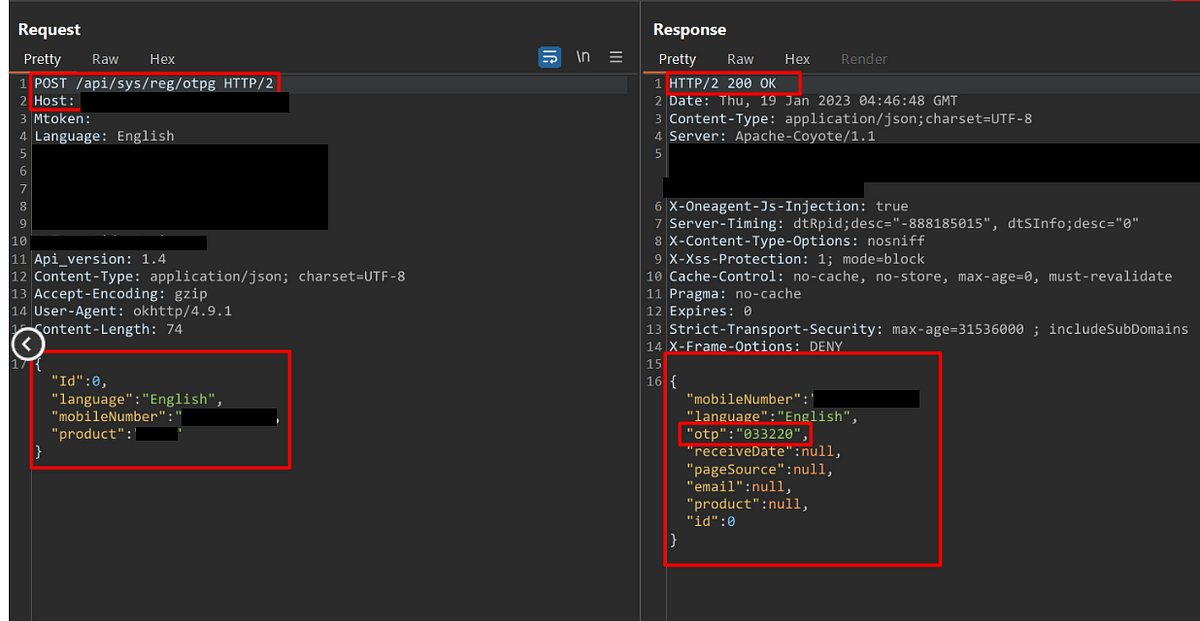
In WebSecurity, cross-site-scripting, Sep 30, 2023Learn and Earn with the Most Common Unsecured Methods of OTP Bypass Techniques.
Discover the ultimate guide for bug bounty hunters to detect sneaky OTP validation vulnerabilities!
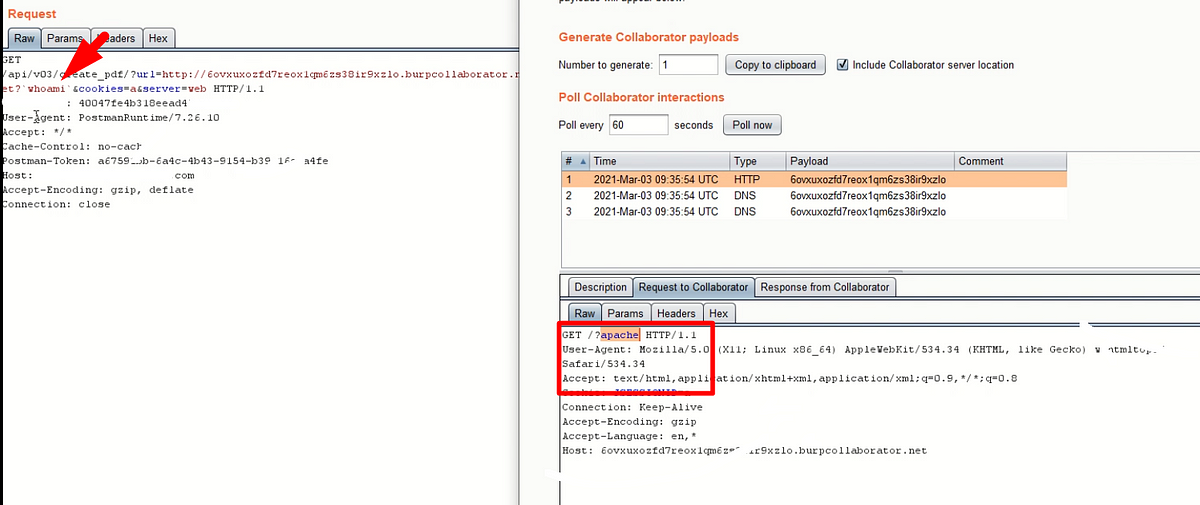
In WebSecurity, APISecurity, Jul 11, 2023The Importance of Checking User-Agent Header Dependency in Penetration Testing.
Never ever give a chance to leave a bug to automated scanners.Introduction:
In WebSecurity, APISecurity, Jun 02, 2023Never leave this tip while you are hunting Broken Access Control.
A special Bug-Bounty tip for Bug hunters and Pen-testers
In WebSecurity, APISecurity, Nov 12, 2021An unknown Linux secret that turned SSRF to OS Command injection.
A weird approach to escalate the Server-Side Request Forgery
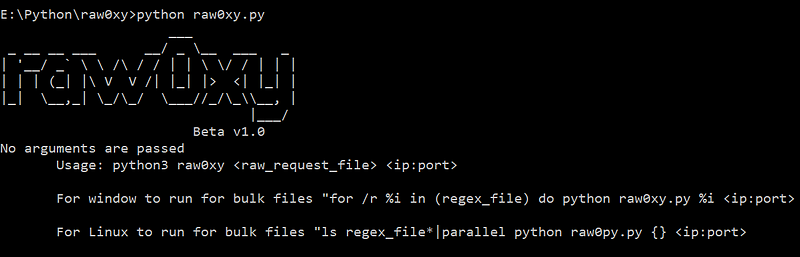
In WebSecurity, APISecurity, Mar 17, 2021Let’s pen-test make easier with raw0xy.
raw0xy is a python script, takes a file that contains raw HTTP request and a proxy route. Then the script will parse the raw HTTP request…
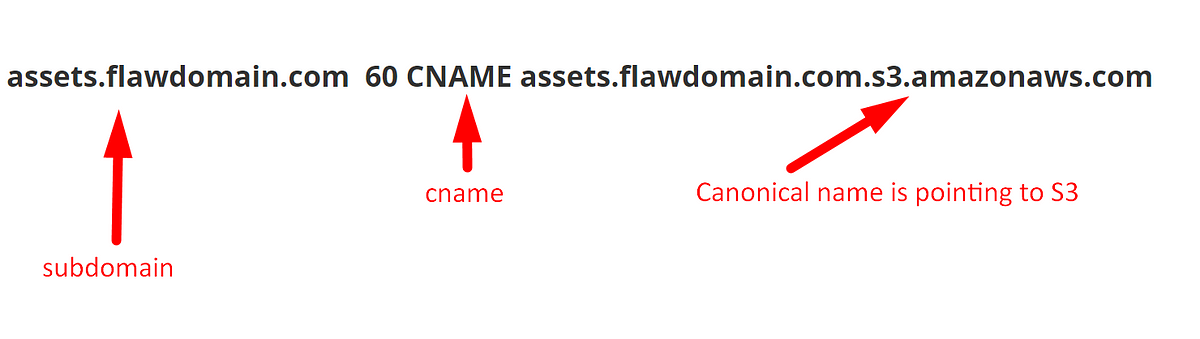
In WebSecurity, APISecurity, Dec 16, 2020Weird “Subdomain Take Over” pattern of Amazon S3.
Even though you have an idea on the subdomain takeover via AWS S3. In this write-up, I will show the non-typical way of S3 subdomain
In WebSecurity, CloudSecurity, May 31, 2020Every Bug Bounty hunter should know the evil smile of the JSONP over the browser’s Same Origin.
JSONP stands for JSON with Padding. It is a JavaScript technique to request the data from the server and can access without worrying about
In WebSecurity, APISecurity, Apr 06, 2020A secret note to Bug hunters about URL structure and its parsers.
Understanding the proper URL structure is important to every Bug bounty hunter. So lets go deep dive into the URL structure.
In WebSecurity, Mar 14, 2020APISecurity
How I perform the JSON CSRF with method override technique.
CSRF(Cross-Site Request Forgery) is a kind of web application vulnerability, using this a malevolent can forge the HTTP request without the actual user knowledge. This will result in ...
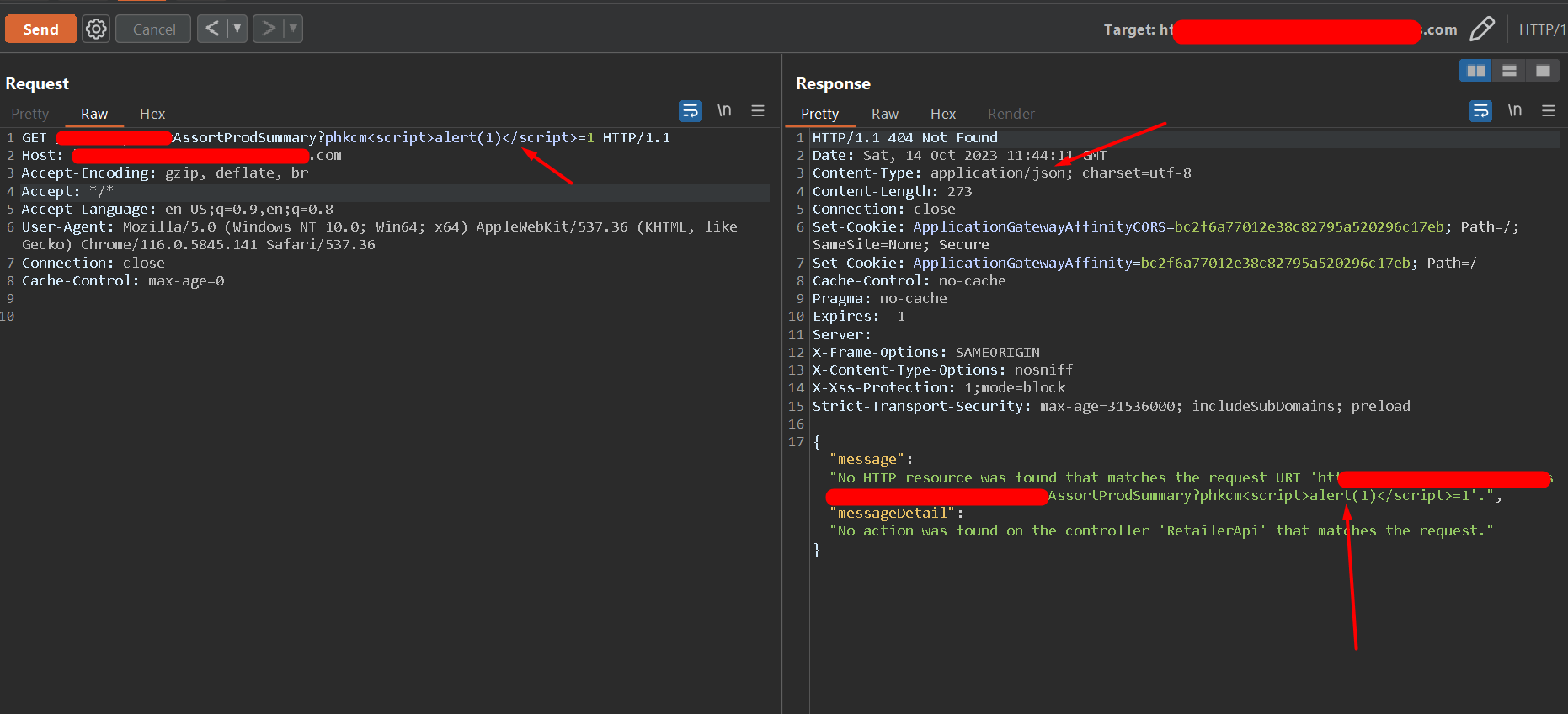
In WebSecurity, APISecurity, Dec 29, 2023Why Appropriate Content-Type Header Matters In REST API Security: Ft. JSON XSS.
Before diving into the specifics of the Content-Type header, let’s quickly recap what REST APIs are all about. REST is an architectural style for designing networked applications. It ...
In APISecurity, XSS, cross-site-scripting, REST-API, Dec 28, 2023Learn and Earn with the Most Common Unsecured Methods of OTP Bypass Techniques.
Discover the ultimate guide for bug bounty hunters to detect sneaky OTP validation vulnerabilities!
In WebSecurity, APISecurity, Jul 11, 2023The Importance of Checking User-Agent Header Dependency in Penetration Testing.
Never ever give a chance to leave a bug to automated scanners.Introduction:
In WebSecurity, APISecurity, Jun 02, 2023Never leave this tip while you are hunting Broken Access Control.
A special Bug-Bounty tip for Bug hunters and Pen-testers
In WebSecurity, APISecurity, Nov 12, 2021An unknown Linux secret that turned SSRF to OS Command injection.
A weird approach to escalate the Server-Side Request Forgery
In WebSecurity, APISecurity, Mar 17, 2021Let’s pen-test make easier with raw0xy.
raw0xy is a python script, takes a file that contains raw HTTP request and a proxy route. Then the script will parse the raw HTTP request…
In WebSecurity, APISecurity, Dec 16, 2020Every Bug Bounty hunter should know the evil smile of the JSONP over the browser’s Same Origin.
JSONP stands for JSON with Padding. It is a JavaScript technique to request the data from the server and can access without worrying about
In WebSecurity, APISecurity, Apr 06, 2020CloudSecurity
Weird “Subdomain Take Over” pattern of Amazon S3.
Even though you have an idea on the subdomain takeover via AWS S3. In this write-up, I will show the non-typical way of S3 subdomain
In WebSecurity, CloudSecurity, May 31, 2020AndroidSecurity
Genymotion-Xposed-Inspeckage-Setup.
Android application dynamic analysis lab setup on windows
In AndroidSecurity, MobileAppPT, Jul 03, 2021Let’s know How I have explored the buried secrets in the Xamarin application.
Mobile Application Penetration Testing Guide
In AndroidSecurity, MobileAppPT, Feb 20, 2021Let’s know How I have explored the buried secrets in React Native application.
Mobile Application Penetration Testing Guide
In AndroidSecurity, MobileAppPT, Jan 18, 2021Hack crypto secrets from heap memory to exploit Android application.
Due to the short time of development, The developers only focus on the building feature, functionalities and UI components. But they may…
In AndroidSecurity, MobileAppPT, Dec 22, 2020Android Hacking Fundamentals -Part-2.
By defalut production build of Android (that’s what you have on your phone until you unlock the bootloader and flash the phone with …
In MobileAppPT, AndroidSecurity, Dec 18, 2020Android Hacking Fundamentals -Part-1.
Before learning about the android application hacking, it is necessary to understand the fundamental concepts of android application files, components and how the different components...
In AndroidSecurity, MobileAppPT, Sep 27, 2020MobileAppPT
Genymotion-Xposed-Inspeckage-Setup.
Android application dynamic analysis lab setup on windows
In AndroidSecurity, MobileAppPT, Jul 03, 2021Let’s know How I have explored the buried secrets in the Xamarin application.
Mobile Application Penetration Testing Guide
In AndroidSecurity, MobileAppPT, Feb 20, 2021Let’s know How I have explored the buried secrets in React Native application.
Mobile Application Penetration Testing Guide
In AndroidSecurity, MobileAppPT, Jan 18, 2021Hack crypto secrets from heap memory to exploit Android application.
Due to the short time of development, The developers only focus on the building feature, functionalities and UI components. But they may…
In AndroidSecurity, MobileAppPT, Dec 22, 2020Android Hacking Fundamentals -Part-2.
By defalut production build of Android (that’s what you have on your phone until you unlock the bootloader and flash the phone with …
In MobileAppPT, AndroidSecurity, Dec 18, 2020Android Hacking Fundamentals -Part-1.
Before learning about the android application hacking, it is necessary to understand the fundamental concepts of android application files, components and how the different components...
In AndroidSecurity, MobileAppPT, Sep 27, 2020secureinfrastructure
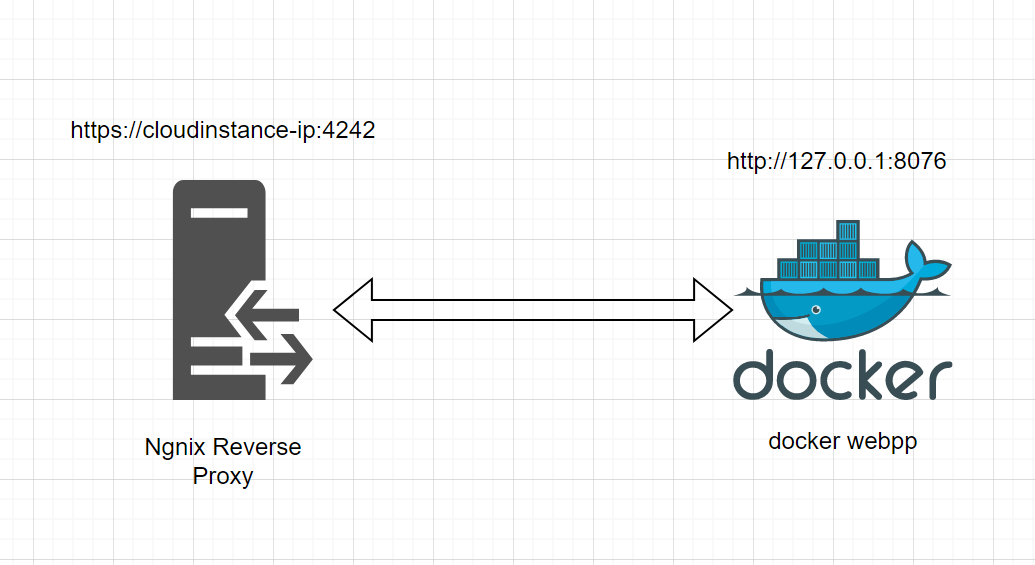
How to secure-docker-instance-with-basic-Authentication
Nginx reverse proxy with Basic Authentication
In secureinfrastructure, Jul 01, 2022How-to-deploy-a-personal-VPN-in-Linode
A better way to take control of your online privacy
In secureinfrastructure, Jul 11, 2021cross-site-scripting
Why Appropriate Content-Type Header Matters In REST API Security: Ft. JSON XSS.
Before diving into the specifics of the Content-Type header, let’s quickly recap what REST APIs are all about. REST is an architectural style for designing networked applications. It ...
In APISecurity, XSS, cross-site-scripting, REST-API, Dec 28, 2023The Art of Identifying X$$ & WAF Bypass Fuzzing Technique.
A smart way to hunt Cross-Site Scripting vulnerability
In WebSecurity, cross-site-scripting, Sep 30, 2023network
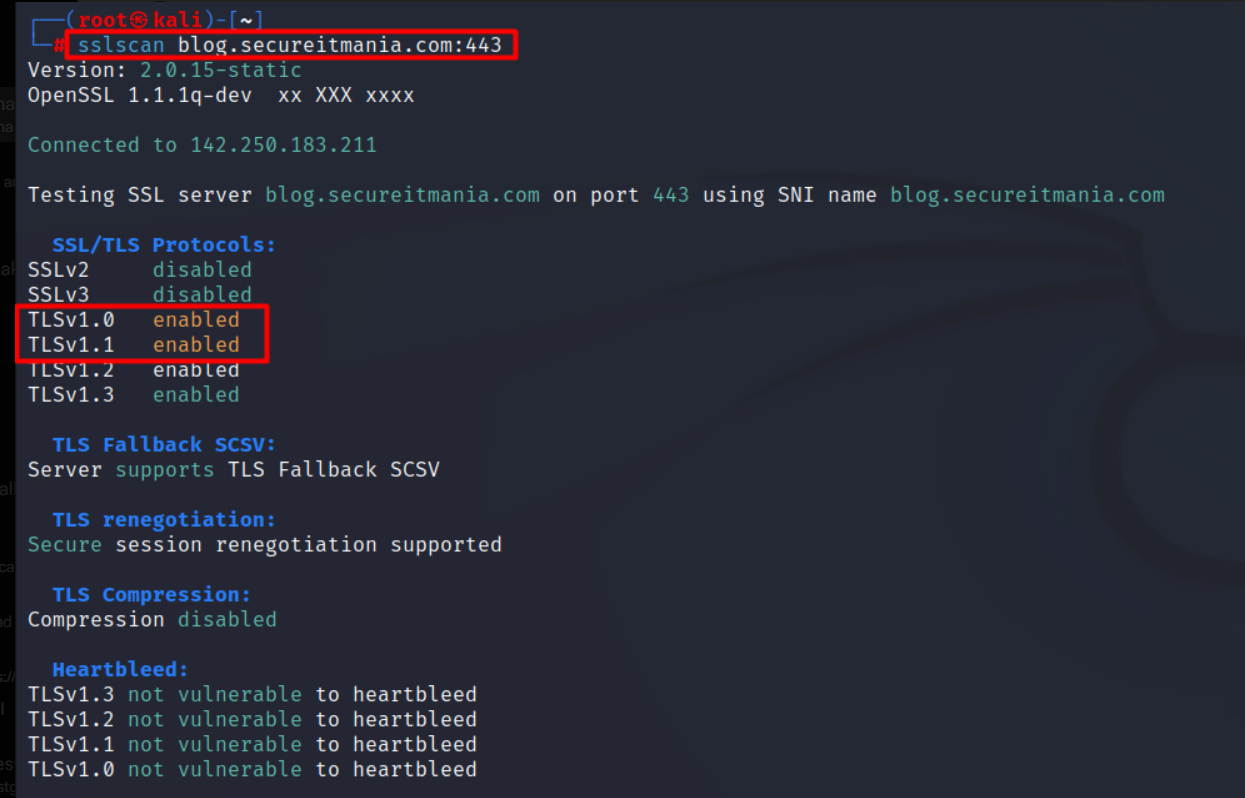
How to analyze the SSL/TLS configuration(sslscan).
SSL/TLS Analysis & Attacks
In network, kali-tool, Dec 28, 2023kali-tool
How to analyze the SSL/TLS configuration(sslscan).
SSL/TLS Analysis & Attacks
In network, kali-tool, Dec 28, 2023XSS
Why Appropriate Content-Type Header Matters In REST API Security: Ft. JSON XSS.
Before diving into the specifics of the Content-Type header, let’s quickly recap what REST APIs are all about. REST is an architectural style for designing networked applications. It ...
In APISecurity, XSS, cross-site-scripting, REST-API, Dec 28, 2023REST-API
Why Appropriate Content-Type Header Matters In REST API Security: Ft. JSON XSS.
Before diving into the specifics of the Content-Type header, let’s quickly recap what REST APIs are all about. REST is an architectural style for designing networked applications. It ...
In APISecurity, XSS, cross-site-scripting, REST-API, Dec 28, 2023