Discover the ultimate guide for bug bounty hunters to detect sneaky OTP validation vulnerabilities!
WEB/API APPLICATION PENETRATION TESTING
Introduction:
As the digital world expands, so does the importance of cybersecurity. One Time Passwords (OTP) have become increasingly popular in the realm of authentication. They are known for providing an extra layer of security, making it difficult for hackers to gain unauthorized access. However, if not properly implemented, OTP validation can leave a system open to various security risks. Let’s explore six of the most common unsecured methods of OTP validation.
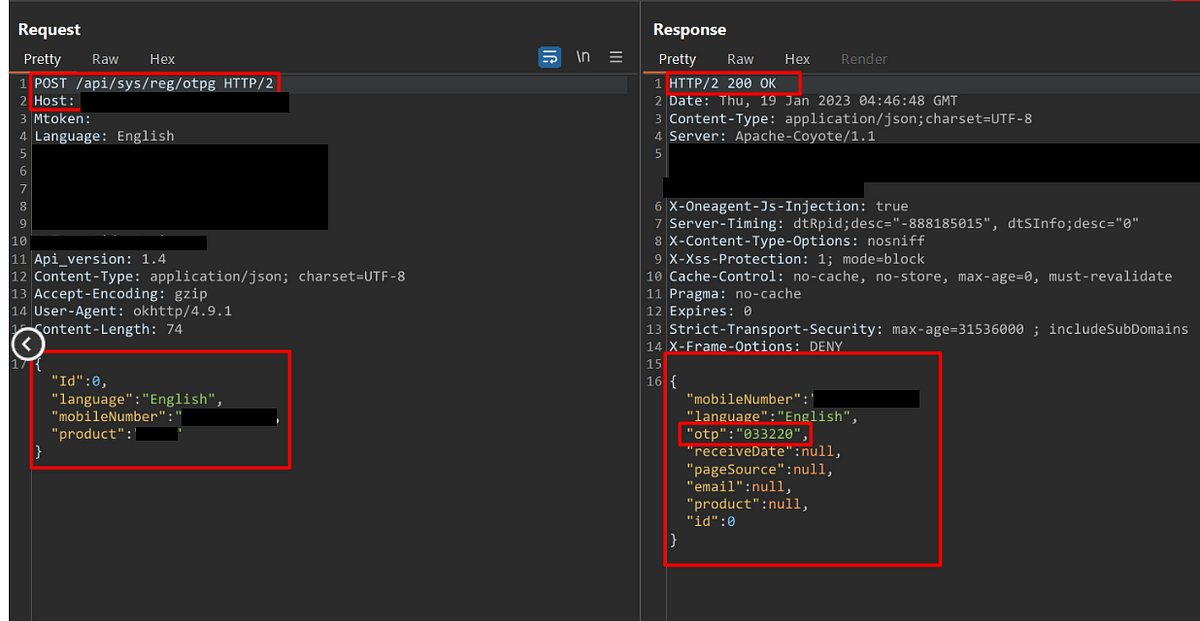
1. OTP Leakage in Response
When the application back-end system generates an OTP, it’s crucial that this information remains confidential. One common insecure practice is when the OTP leaks through server responses. This can happen when the OTP, once generated, is included in HTTP responses, logs, or error messages that can be intercepted by attackers. Ensuring OTPs are kept hidden in responses is key to maintaining their integrity and confidentiality.
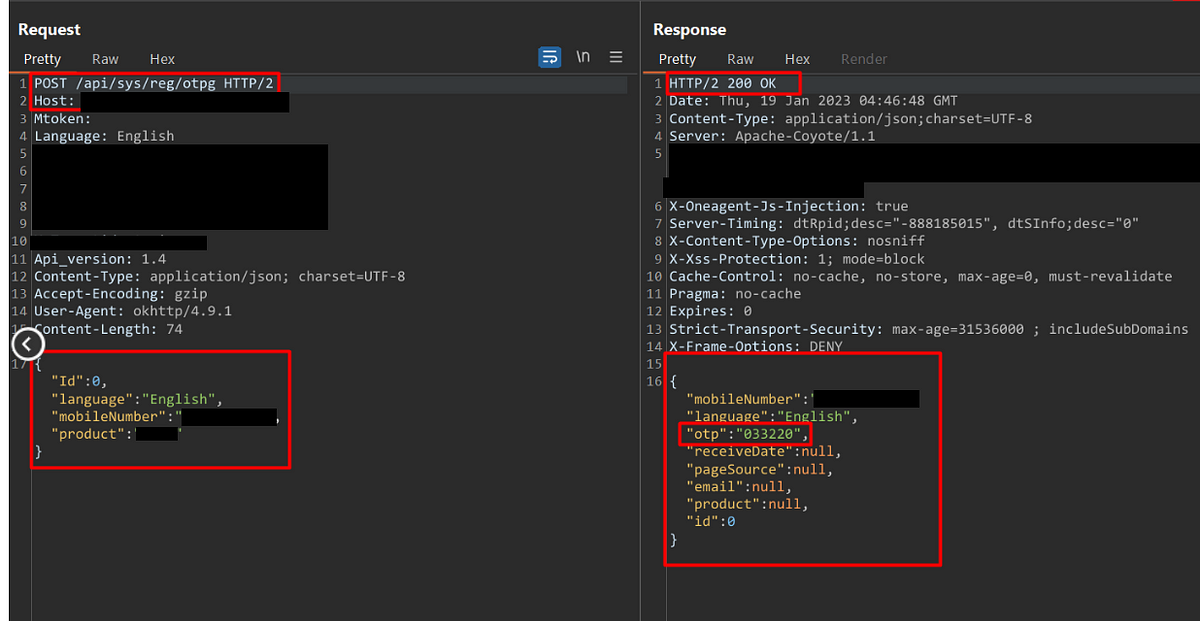
2. Weak OTP Length
The length and complexity of an OTP significantly impact its security. A short OTP 4 & 5 digit or one without a mixture of characters, numbers, and symbols can easily be cracked by brute force attacks. As a rule of thumb, OTPs should be of sufficient length (at least six characters) and complexity, involving a mix of alphanumeric and special characters.
3. Insecure OTP Validation logic on the server side.
In an ideal scenario, once a user enters the OTP, the system checks it on the server side for validation and only then grants access to certain actions or information. However, when this process is misconfigured, it can lead to substantial security vulnerabilities. A significant misstep is when the OTP state is insecurely validated on the server side.
Let’s consider a scenario where the server validates the OTP and sends back a static success message, such as { “otp_validation”: true, “statusCode”: 200 }. Once the client application receives this message, it opens access to certain sensitive actions for the user. For instance, the user might be able to change their password, modify their email, or update their mobile number.
The crux of the problem here is that the system does not re-verify whether the user’s OTP was genuinely validated for these sensitive actions. The system assumes that the OTP must have been correctly entered and validated if these actions are being accessed.
In this configuration, a malicious user can exploit this loophole. For example, they can intercept the server response and replace it with a seemingly legitimate success response, bypassing the OTP validation entirely. Since the system does not recheck OTP validation on the server side during these sensitive operations, the manipulated response goes unnoticed, granting the user unwarranted access.
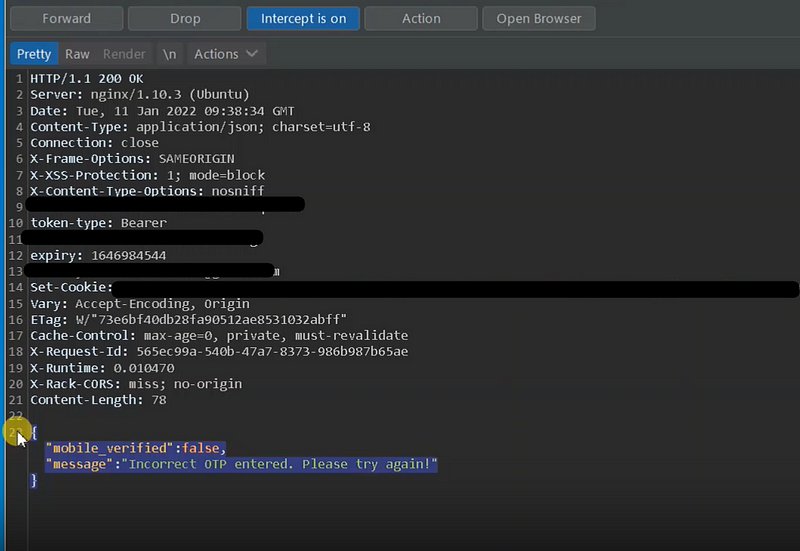
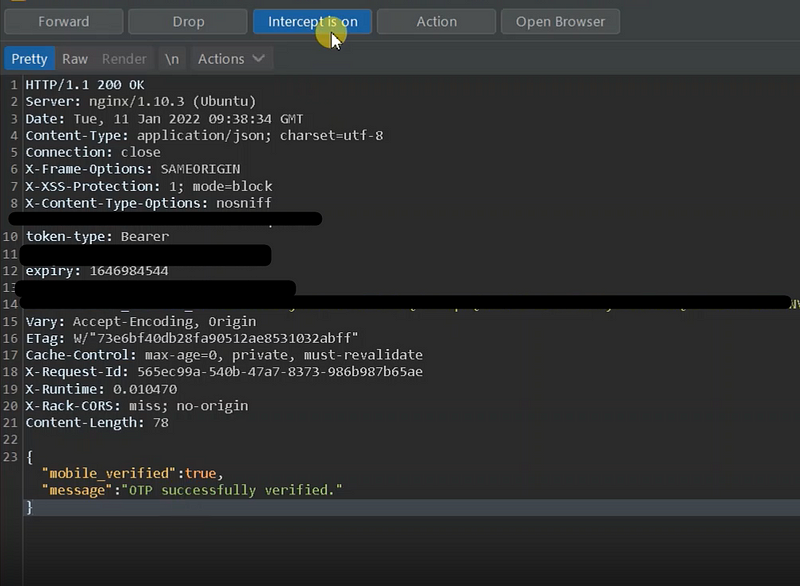
4. Lack of OTP Expiration
Without an expiration time, OTPs are vulnerable to replay attacks. In such attacks, an old, intercepted OTP could be used for unauthorized access. To mitigate this risk, OTPs should be time-sensitive, usually expiring within a few minutes of being issued. After the given time, they should be rendered useless, thus invalidating any attempts at unauthorized access.
5. Reuse of OTP
Each OTP should be unique and not reusable. This would limit the scope of a potential attack, even if an OTP were to be compromised. Once an OTP is used, it should immediately become invalid. If an OTP can be used more than once, it allows an opportunity for hackers to gain unauthorized access.
6. Static Token Generation after OTP Validation
In this case, a common insecure practice is generating static tokens, such as a username’s MD5 hash value, as a session token after OTP validation. Because this value doesn’t change over time, it can provide perpetual access to the hacker if it’s compromised once. To avoid this, session tokens should be dynamic, random, and expire after a certain period of inactivity.
Conclusion:
In conclusion, while OTPs offer an added layer of security, their implementation must be carefully executed to avoid pitfalls. Employing best practices in OTP validation and understanding common security risks can significantly help strengthen a system’s security. In a digital era where cyber threats are ever-evolving, we must continue refining and enhancing our security measures to stay one step ahead.
 The Importance of Checking User-Agent Header Dependency in Penetration Testing.
The Importance of Checking User-Agent Header Dependency in Penetration Testing.