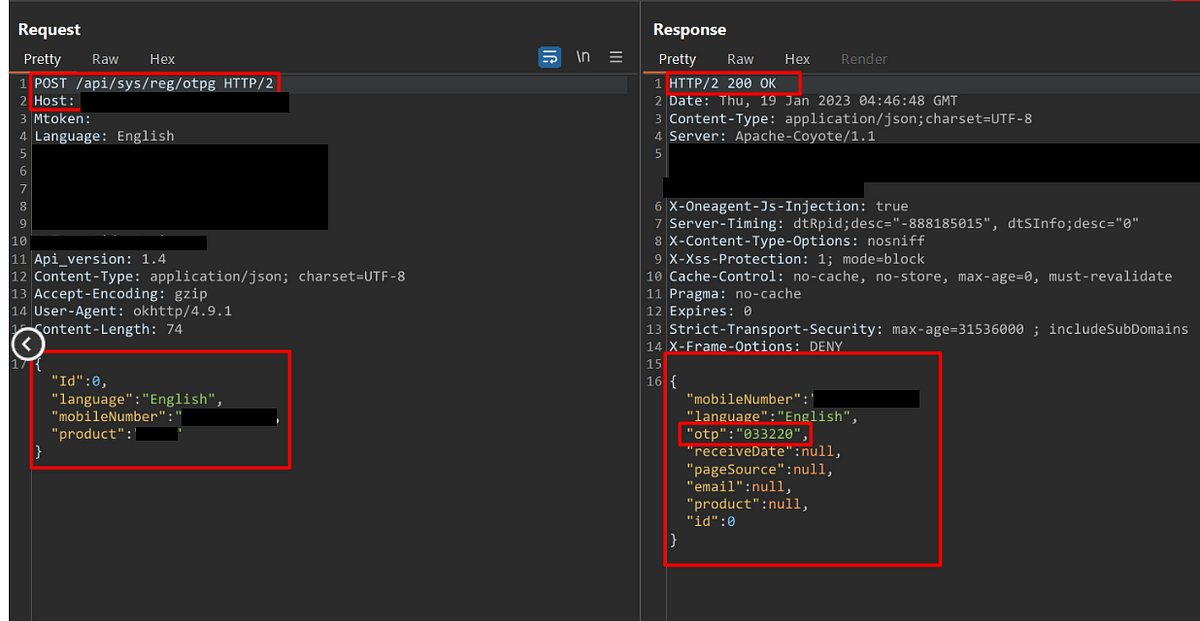
Never ever give a chance to leave a bug to automated scanners.
Introduction:
In the world of penetration testing, it is crucial to employ the right tools and methodologies to uncover vulnerabilities in a system. However, blindly relying on security tools without considering certain factors can lead to false positive results, wasting valuable time and resources. One such factor that requires careful analysis is the User-Agent header dependency. In this article, we will explore why it is essential to check if a server is “User-Agent header dependent” and the implications it has on automated scanning tools like sqlmap, dirsearch, and other bash tools.
Understanding User-Agent Header Dependency:
The User-Agent header is a part of the HTTP request header that provides information about the client making the request. It typically includes details such as the user’s operating system, browser, and version. The server can utilize this information to deliver content optimized for the requesting client.
Some servers implement User-Agent header validation as a security measure. This means that they expect specific User-Agent strings to be present in the requests, and if they are not, the server may respond differently or even reject the request altogether. This approach helps prevent unauthorized access and can serve as a defense against certain types of attacks.
How to Analyzing Headers Dependency:
To ensure accurate and reliable results during penetration testing, it is crucial for testers to analyze the headers dependency of the target server.
First analyze the response with User-Agent Header in the request.
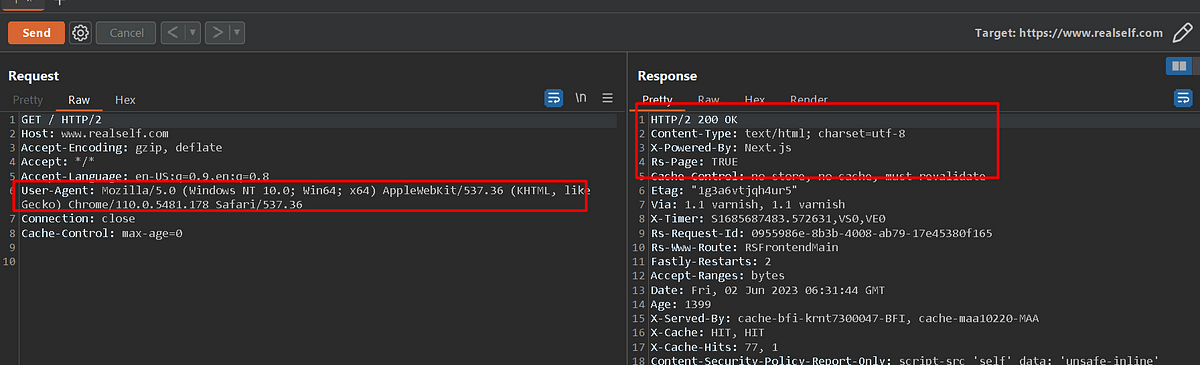
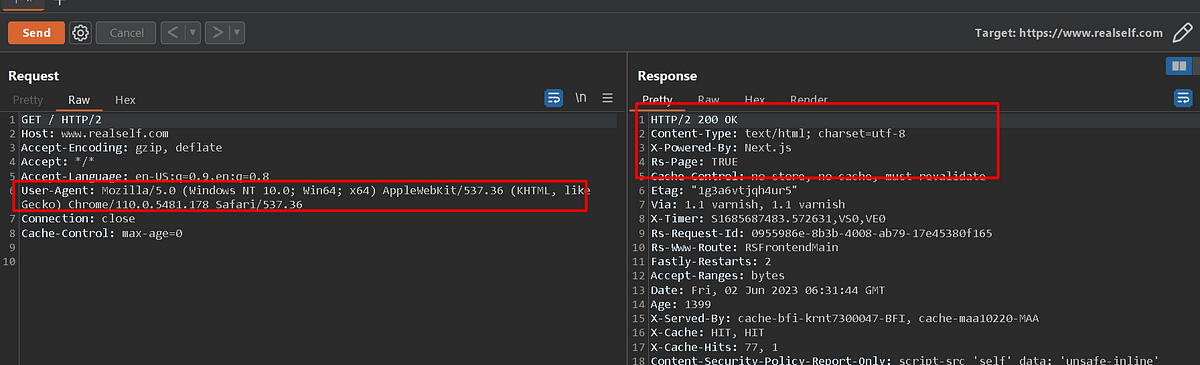
Then, send the request by removing the “User-Agent Header” from the request. If the server response differs from the original request, then the server is expecting the “User-Agent” header strictly.
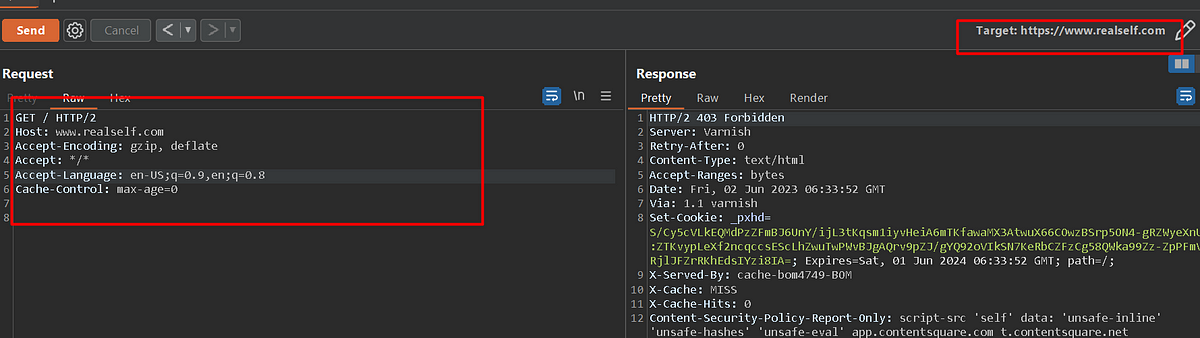
Explore Automated tool usage and its features wisely
Once the User-Agent header dependency is identified, testers can enhance the effectiveness of automated scans by adding expected specific User-Agent strings. Most security tools offer the option to customize headers. For example, in the case of sqlmap, the --headers argument can be utilized to include the desired User-Agent string in the request header. Similarly, other tools like dirsearch and various bash scripts provide similar options to modify headers.
Examples:
- sqlmap: To incorporate a specific User-Agent string using sqlmap, the following command can be used:
sqlmap -u http://target.com/vulnerable_page.php –headers=”User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.3
By specifying the custom User-Agent string, sqlmap ensures that the server response accurately reflects the behavior of the targeted user agent.
2. dirsearch: When using dirsearch, the User-Agent string can be modified using the “-H” or “ — headers” option.
python3 dirsearch.py -u http://target.com -H “User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.3”
This allows dirsearch to simulate requests from a specific User-Agent, improving the reliability of the scan results.
Conclusion:
Penetration testing is a critical aspect of ensuring the security of systems and networks. However, false positive results can occur if the server is dependent on User-Agent headers. To mitigate this issue, penetration testers should carefully analyze the dependency and add custom User-Agent strings before conducting automated scans. By considering this aspect, testers can enhance the accuracy of their tests and obtain more reliable results, leading to improved security measures and better protection against potential vulnerabilities.
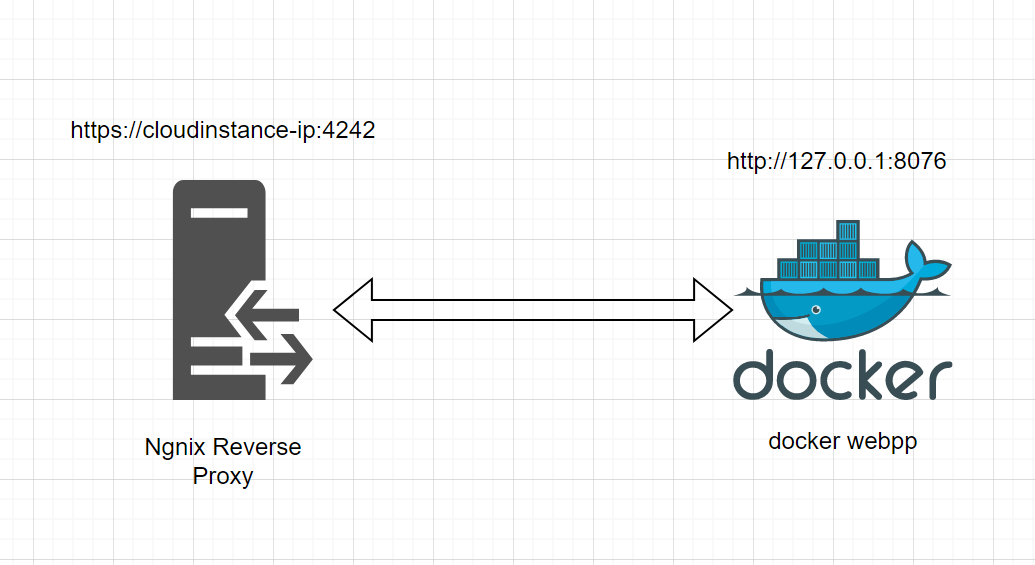 How to secure-docker-instance-with-basic-Authentication
How to secure-docker-instance-with-basic-Authentication