A smart way to hunt Cross-Site Scripting vulnerability
Introduction
Cross-site scripting (XSS) vulnerabilities are among the most common security issues in web applications today. Exploiting an XSS vulnerability allows an attacker to inject malicious scripts into a trusted website, potentially compromising user data, session cookies, and even the entire application. To effectively hunt for XSS vulnerabilities, you need a systematic approach, especially when dealing with Web Application Firewalls (WAFs). In this article, we’ll explore the art of hunting XSS vulnerabilities and discuss techniques for bypassing WAFs.
1. Detect the WAF
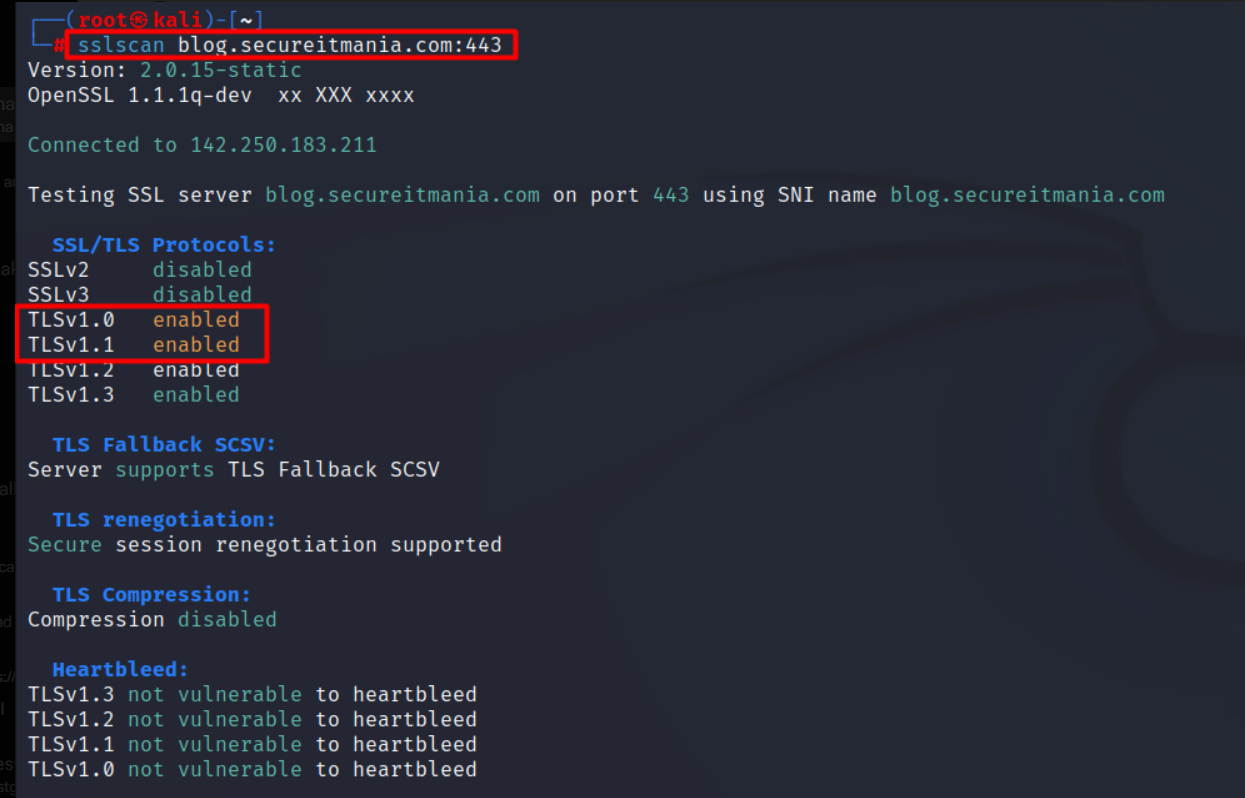
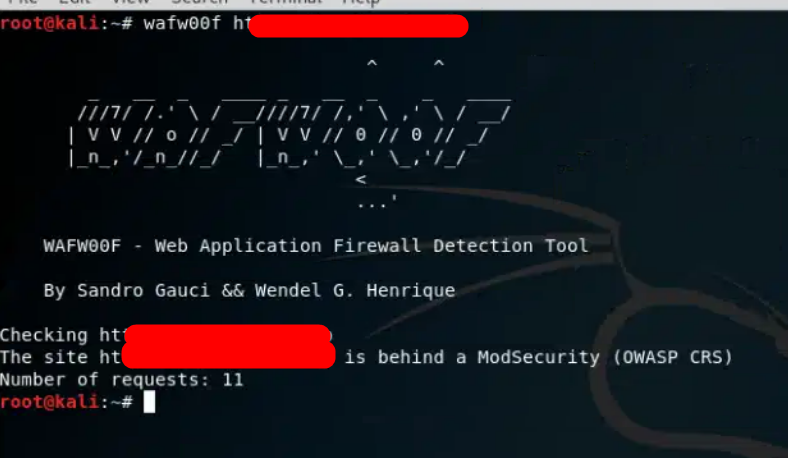
Before you start hunting for XSS vulnerabilities, it’s crucial to confirm if the target application is behind a Web Application Firewall (WAF). WAFs are security systems that filter and monitor incoming web traffic, designed to protect web applications from various attacks, including XSS. In order to begin your hunting process, it’s important first to determine whether or not a WAF is present.

2. Use Basic HTML Injection Payloads
Once you’ve confirmed the presence of a WAF, it’s a good practice to start with basic HTML injection payloads. These payloads are intentionally simple and benign, designed to test whether the application is susceptible to injection.
<h1>test</h1>
<a>click here</a>
<title>test</title>
The goal is to determine whether the application reflects or executes the injected code without WAF interference. If the application behaves unexpectedly or displays the payload, it’s a sign that an XSS vulnerability may exist.

3. Elevating from HTML Injection to XSS
Once you’ve confirmed HTML injection in any input field, you can proceed to evaluate whether it can be escalated into a full-blown XSS vulnerability.
Here the WAF has detected the XSS payload and restricted it.

4. Fuzz with WAF Bypass payload
First, we need to collect common XSS WAF bypass payloads and add them to the Intruder payload list. After that, we can use the Burp Suite intruder to fuzz the vulnerable parameter. The below GitHub repo is my favourite one.
XSS payloads for bypassing WAF.
Filter “200” Status code response requests, which means the payload is successfully injected without any WAF restriction.

Try the filtered requests from the browser and observe the JavaScript execution.

Conclusion:
When searching for Cross-Site Scripting vulnerabilities, it’s important to have a methodical approach that considers the existence of Web Application Firewalls. This involves beginning with simple HTML injection payloads, progressing to more complex XSS payloads, and utilizing evasion techniques to surpass WAF limitations.
Join my telegram channel for more BugBounty and Cyber Security free tips.
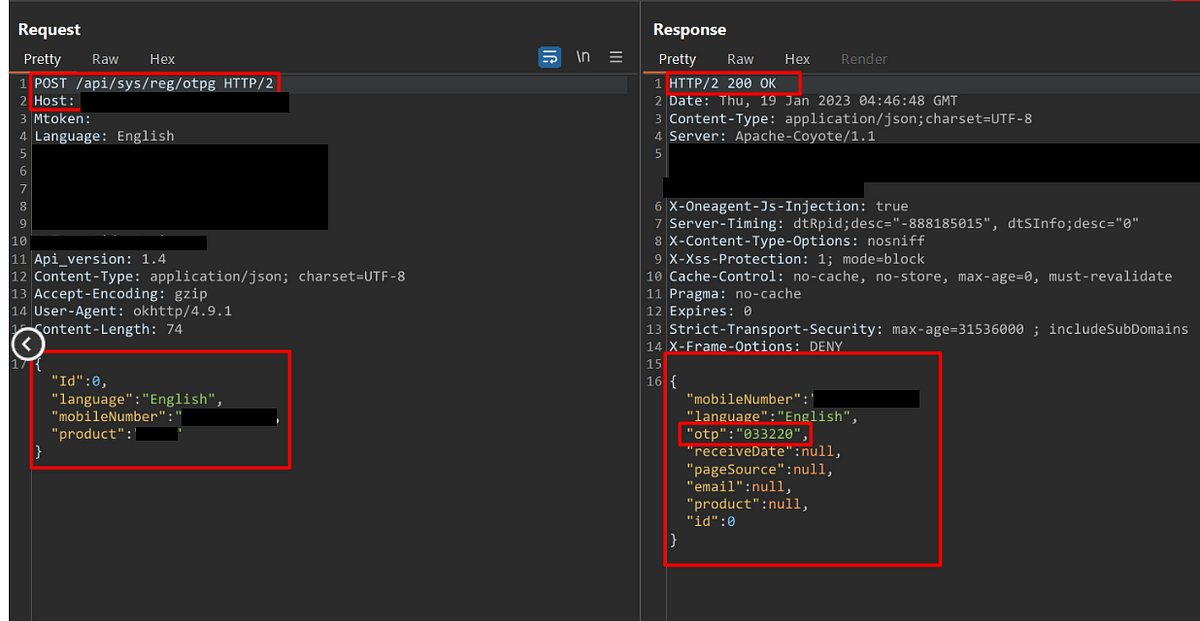 Learn and Earn with the Most Common Unsecured Methods of OTP Bypass Techniques.
Learn and Earn with the Most Common Unsecured Methods of OTP Bypass Techniques.