SSL/TLS Analysis & Attacks
Vulnerabilities
- Weak Protocols Enabled (SSLv2, SSLv3, TLSv1.0, TLSv1.1)
- Heartbleed Attack
- Weak signature algorithm
- TLS 1.2 Vulnerabilities
- Secure Client-Initiated Renegotiation
- Expired SSL Certificate
To scan the website use the below sslscan command
sslscan --show-sigs target.com:port
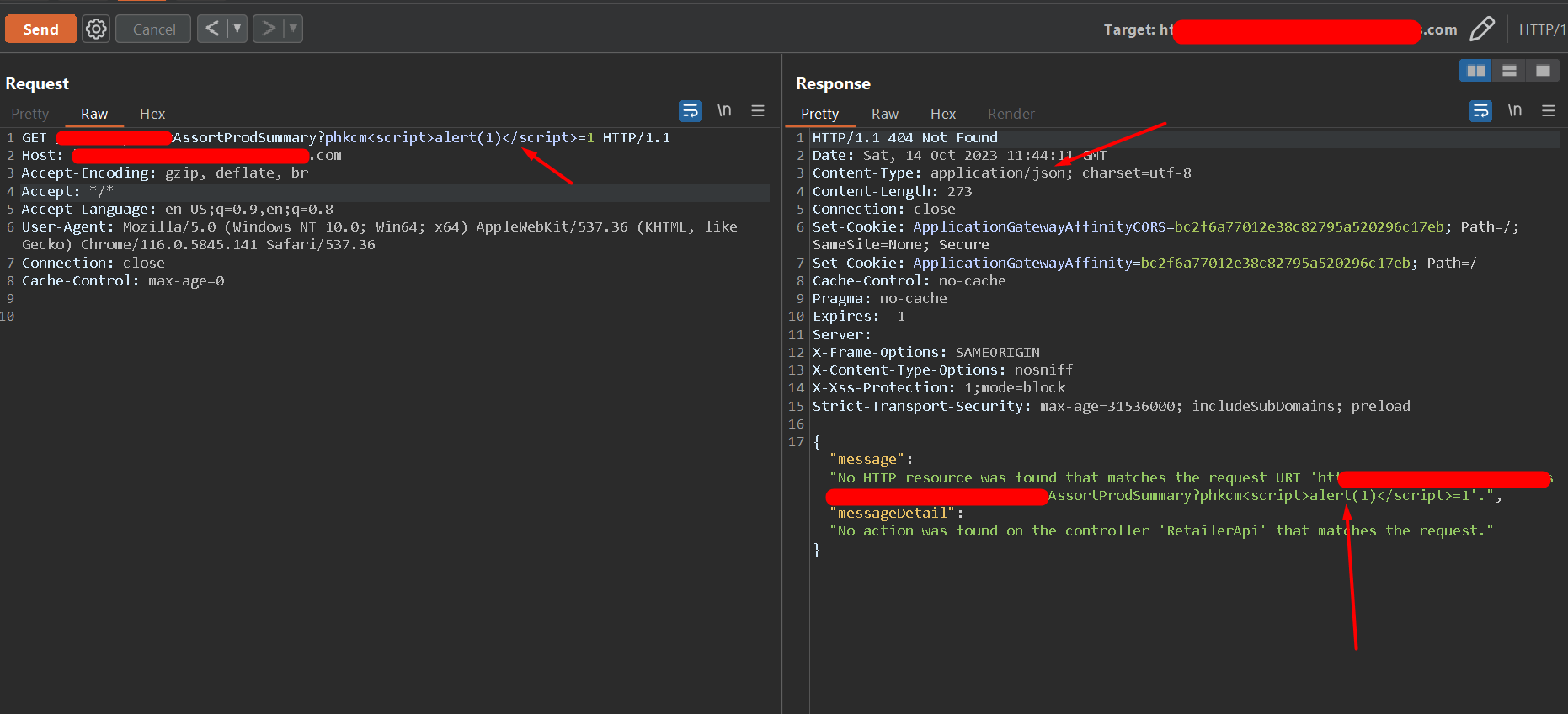
Weak Protocols Enabled
SSLv2, SSLv3, TLS 1.0 & TLS 1.1 protocols are considered as weak protocols.
The above protocols are vulnerable to several attacks such as DROWN Attack, POODLE Attack, BEAST Attack, Renegotiation Attack, Lucky Thirteen and SWEET32

Heartbleed Attack
Heartbleed is a serious vulnerability in the widely used OpenSSL cryptographic software library. It was publicly disclosed in April 2014 and quickly gained notoriety due to its severe impact
The vulnerability arises from a missing bounds check in the handling of the Heartbeat extension. When a client sends a Heartbeat request, it specifies the length of the payload. The server is supposed to send back the same payload, demonstrating that it’s still alive.
The problem in the vulnerable versions of OpenSSL is that the server does not verify that the specified length is correct. An attacker can specify a length that is longer than the actual payload, and the server will respond with not only the original payload but also additional data from the server’s memory, up to the length specified

Weak signature algorithm
Security Concerns: Accepting all signature algorithms without restrictions can introduce security risks, particularly if weak or compromised algorithms are included. Signature algorithms play a crucial role in authenticating the connection, and weak algorithms can be vulnerable to attacks.
Compliance Issues: Depending on the industry and regulatory environment, there may be specific requirements for cryptographic algorithms, and accepting all without discrimination might lead to non-compliance.
In general, it’s advisable to configure servers to accept only well-vetted and strong signature algorithms. By limiting the accepted algorithms to those known to be secure, you reduce the risk of an attacker exploiting a weak algorithm to compromise the connection.

TLS 1.2 Vulnerabilities
TLS 1.2 was a significant improvement over earlier versions, addressing many known vulnerabilities. However, like any complex cryptographic protocol, it is not entirely immune to potential attacks. Some of the notable issues that have been identified in TLS 1.2 include:
- CRIME (Compression Ratio Info-leak Made Easy)
- BREACH (Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext)
- Lucky 13 (CBC mode ciphers)
- RC4 Bias Vulnerabilities
- DROWN (Decrypting RSA with Obsolete and Weakened eNcryption)
- Renegotiation Attacks
- FREAK (Factoring RSA Export Keys)
Download and install the testssl.sh tool
./testssl.sh --quiet -C -B -L -4 -F -D -R target.com:port

Only report “Lucky13” vulnerability if you identify any CBC ciphers in the TLS1.2 ciphers. This is because fixing the weak protocol issues in TLS1.0 and TLS1.1 will also fix the Lucky13 vulnerability if the CBC ciphers are avaiable in this protocols.

Secure Client-Initiated Renegotiation DOS

How to check manually
openssl s_client -connect target.com:port
Once you have an established connection, you can initiate a renegotiation by typing R and pressing enter.
If it’s enabled, you will see a ‘RENEGOTIATING’ message, and the connection is still open.

Expired SSL Certificate
An expired SSL certificate can lead to several issues and concerns, both from a security standpoint and from a user experience perspective:
- Loss of Trust: Certificates are time-bound to ensure that the keys they use are not compromised over time. An expired certificate may be seen as untrustworthy.
- Potential for Attack: Expired certificates could potentially be more susceptible to certain attacks, such as man-in-the-middle (MITM) attacks.
- Non-Compliance: Various regulations and standards may require up-to-date encryption and authentication. An expired certificate may result in non-compliance, leading to penalties or legal issues.
- Browser Warnings: Modern web browsers display warning messages when a user attempts to visit a site with an expired certificate. This can create fear and distrust, leading users to abandon the site.

 The Art of Identifying X$$ & WAF Bypass Fuzzing Technique.
The Art of Identifying X$$ & WAF Bypass Fuzzing Technique.