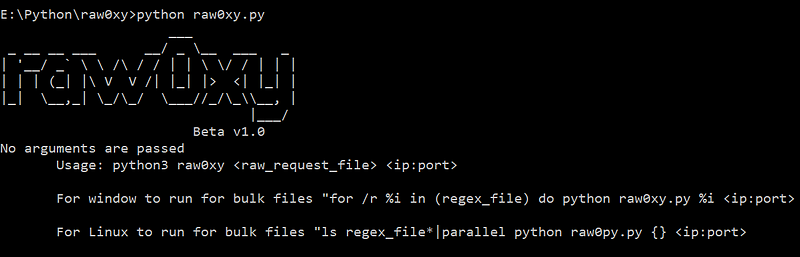
raw0xy is a python script, takes a file that contains raw HTTP request and a proxy route. Then the script will parse the raw HTTP request…
In the recent android application penetration testing, I have encountered a challenge. In that, I have to copy-paste hundreds of file content to BurpSuite. So I frustrated with this copy-paste task and finally, I wrote a script and named it as raw0xy.
What is raw0xy:
raw0xy is a python script, takes a file that contains raw HTTP request and a proxy route. Then the script will parse the raw HTTP request and sends it via defined proxy.

Where and How can I use raw0xy:
In the mobile application penetration testing, I often experience certificate pinning issue. Due to this, I may fail to intercept the application traffic through BurpSuite. In that case, I use HTTPCanary to capture raw HTTP requests by hooking the target application. Using HTTPCanary, I gather raw HTTP requests and export those text files to PC.
With a directory full of raw HTTP requests it was time to import them into BurpSuite and start analysis on those requests. However I could not find any method or extension of importing my raw HTTP requests into BurpSuite other than manually copying and pasting them into repeater. This is the place where I frustrated to do repeated task.
After a short break I got an idea like this “By simply send the raw HTTP request through BurpSuite by sending them from a python script with a proxy configured.”
Never send a human to do a machine’s job
Using my noob python script coding level and by sniffing code snippets from stackoverflow 😜 I made a tool to achieve the above task and named it 😎raw0xy😎.
secureITmania/raw0xy
_Tool Information In the recent android application testing, I encountered a challenge. That is import raw HTTP request…_github.com
Tool Usage:
usage:
cat test.txt
GET /test h2
Host: www.google.com
user-agent: Mozilla/5.0 (Linux; Android 8.1.0; Nexus 5X Build/OPM4.171019.016.A1; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/61.0.3163.98 Mobile Safari/537.36
accept: image/webp,image/apng,image/*,*/*;q=0.8
referer: http://localhost/
accept-encoding: gzip, deflate
accept-language: en-US
python raw0xy.py test.txt 127.0.0.1:8052
At present the tool doesn’t have the multi-threading capability. But we can use in build system capabilities to run on bulk files.
For Windows:for /r %i in (file_name_regex*) do python raw0xy.py %i <ip:port>For Linux:ls file_name_regex*|parallel python raw0py.py {} <ip:port>
Thanks for reading. If you like this content please do follow me and stay tune for more hacking techniques and work productivity hacks
Checkout my previous write-up that explain the technique of subdomain takeover of s3.
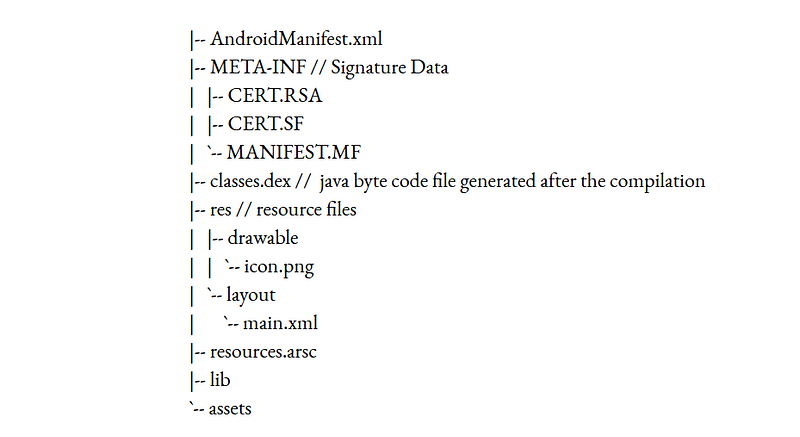 Android Hacking Fundamentals -Part-1.
Android Hacking Fundamentals -Part-1.