All Stories
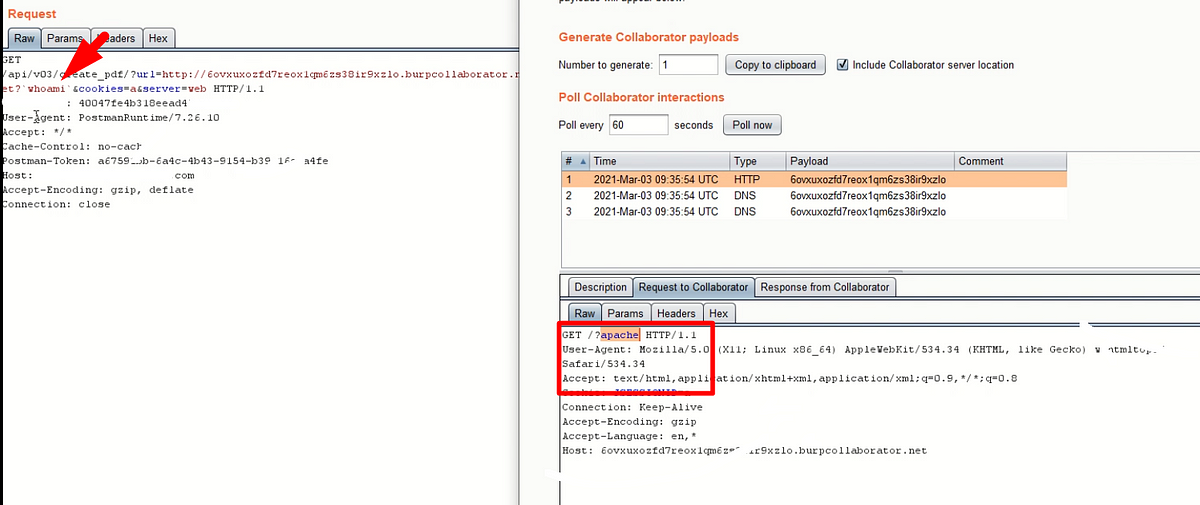
An unknown Linux secret that turned SSRF to OS Command injection.
A weird approach to escalate the Server-Side Request Forgery
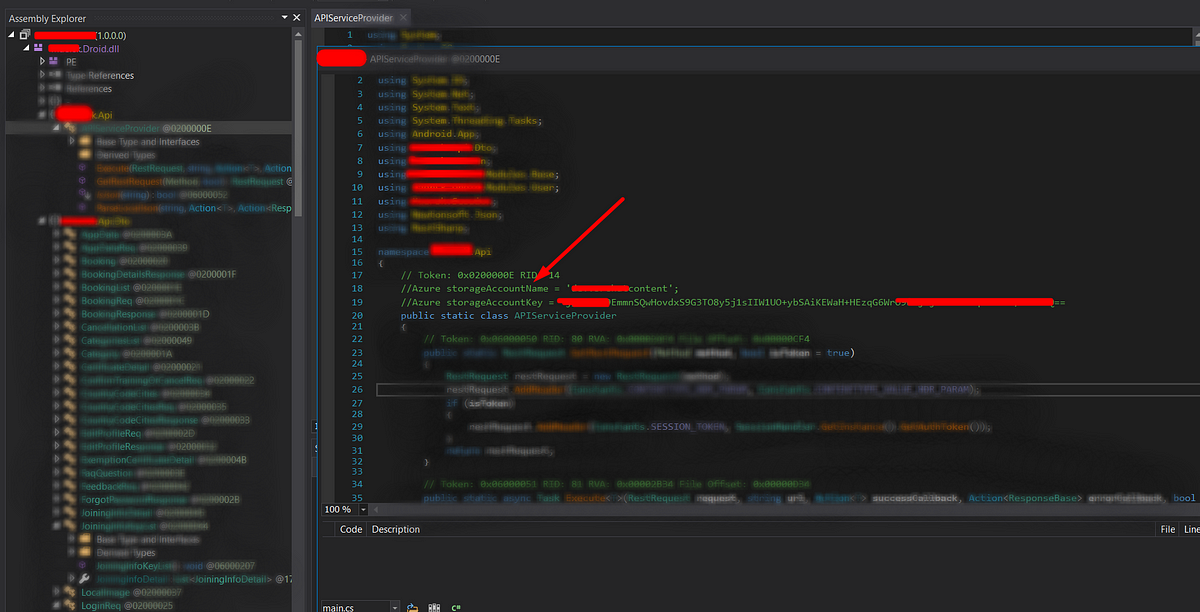
In WebSecurity, APISecurity, Mar 17, 2021Let’s know How I have explored the buried secrets in the Xamarin application.
Mobile Application Penetration Testing Guide
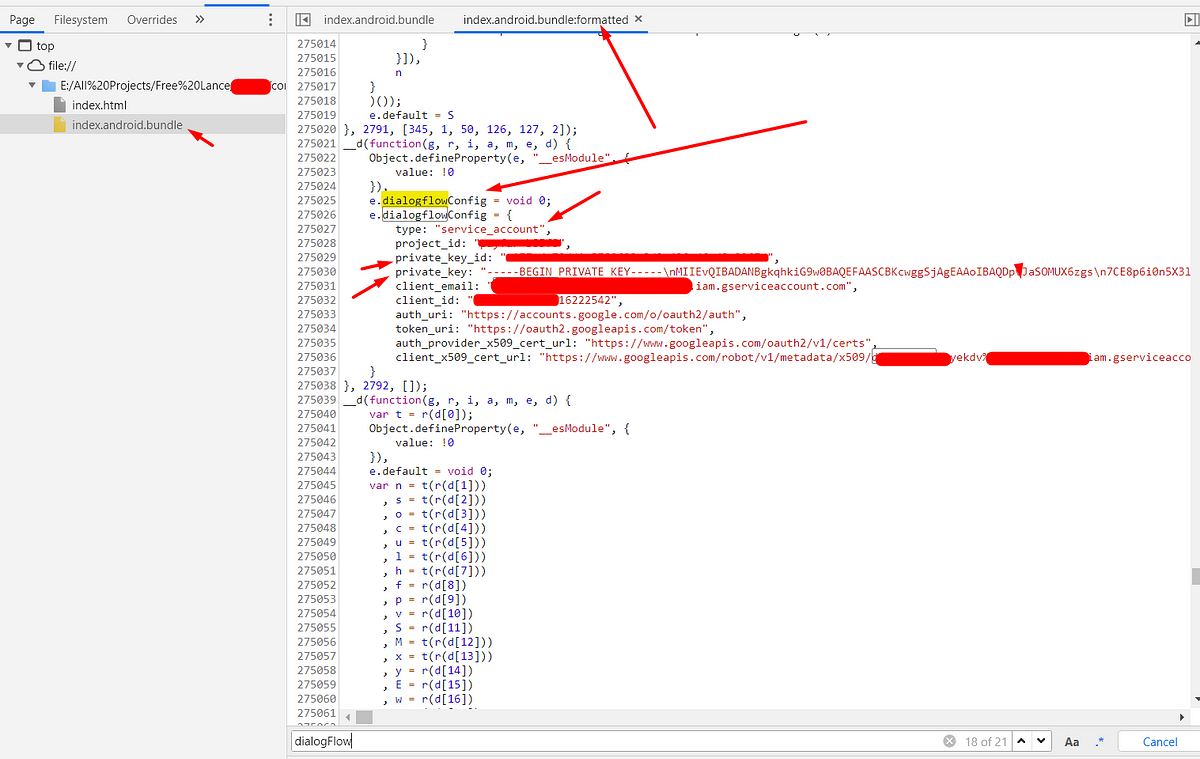
In AndroidSecurity, MobileAppPT, Feb 20, 2021Let’s know How I have explored the buried secrets in React Native application.
Mobile Application Penetration Testing Guide
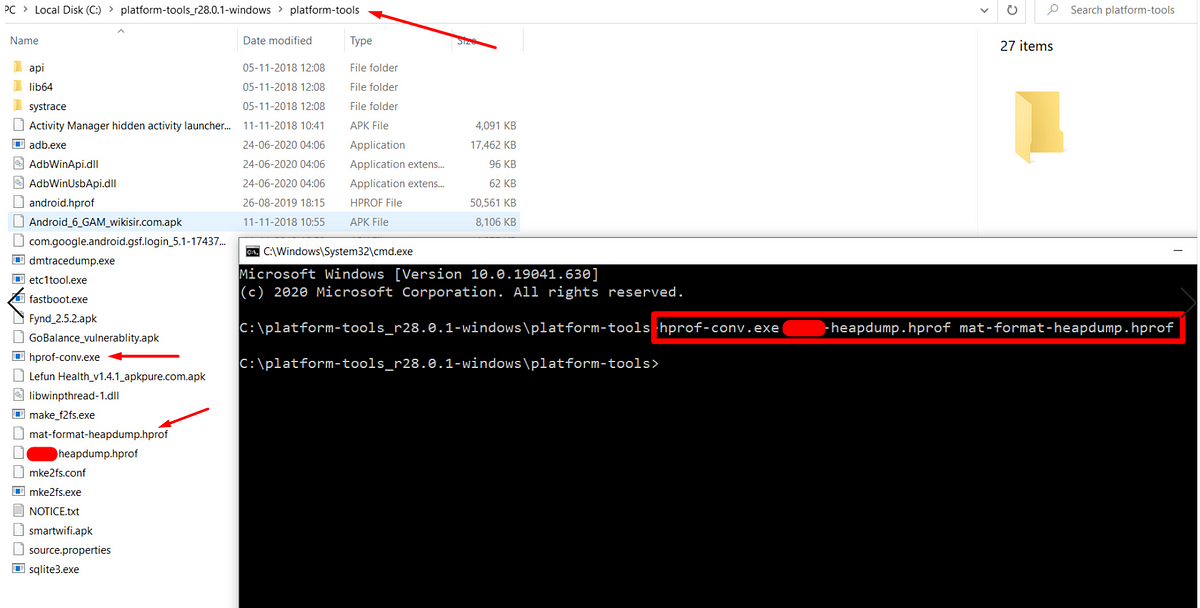
In AndroidSecurity, MobileAppPT, Jan 18, 2021Hack crypto secrets from heap memory to exploit Android application.
Due to the short time of development, The developers only focus on the building feature, functionalities and UI components. But they may…
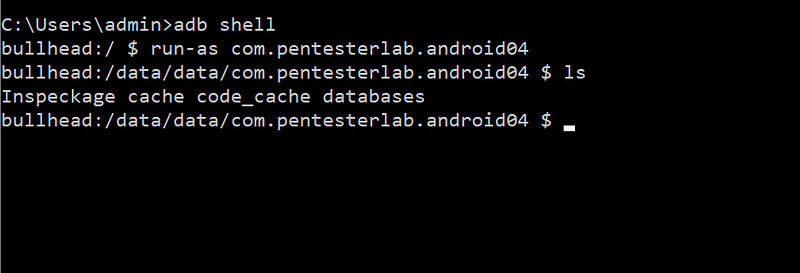
In AndroidSecurity, MobileAppPT, Dec 22, 2020Android Hacking Fundamentals -Part-2.
By defalut production build of Android (that’s what you have on your phone until you unlock the bootloader and flash the phone with …
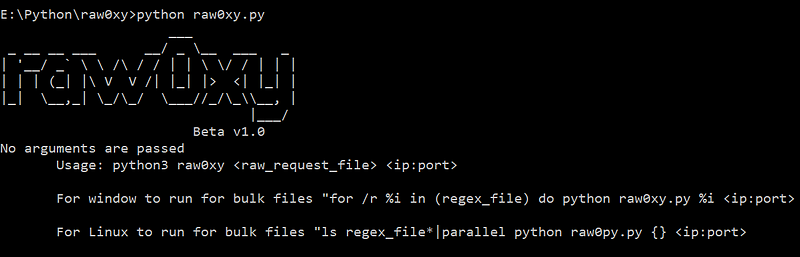
In MobileAppPT, AndroidSecurity, Dec 18, 2020Let’s pen-test make easier with raw0xy.
raw0xy is a python script, takes a file that contains raw HTTP request and a proxy route. Then the script will parse the raw HTTP request…
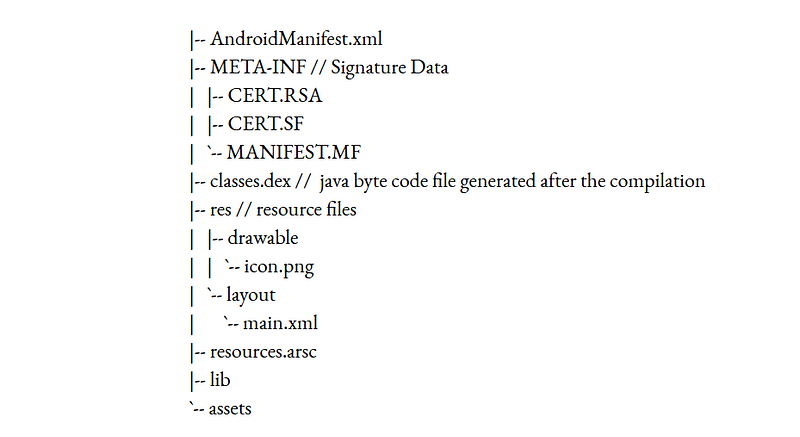
In WebSecurity, APISecurity, Dec 16, 2020Android Hacking Fundamentals -Part-1.
Before learning about the android application hacking, it is necessary to understand the fundamental concepts of android application files, components and how the different components...
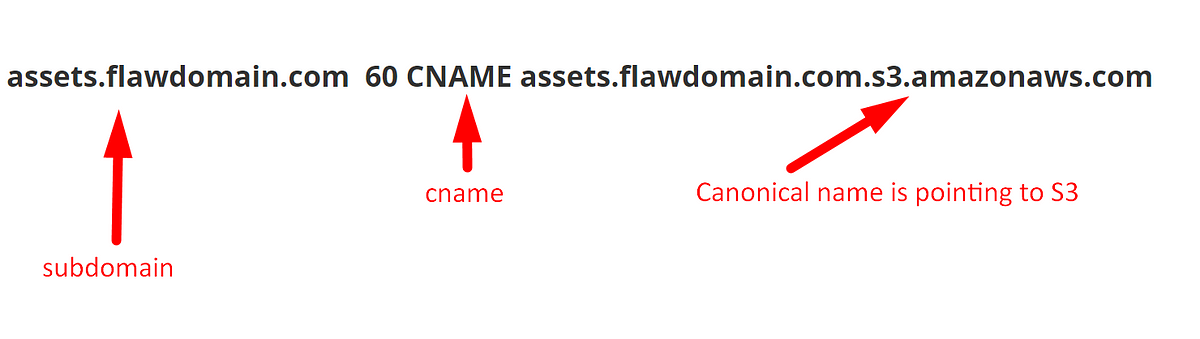
In AndroidSecurity, MobileAppPT, Sep 27, 2020Weird “Subdomain Take Over” pattern of Amazon S3.
Even though you have an idea on the subdomain takeover via AWS S3. In this write-up, I will show the non-typical way of S3 subdomain
In WebSecurity, CloudSecurity, May 31, 2020Every Bug Bounty hunter should know the evil smile of the JSONP over the browser’s Same Origin.
JSONP stands for JSON with Padding. It is a JavaScript technique to request the data from the server and can access without worrying about
In WebSecurity, APISecurity, Apr 06, 2020A secret note to Bug hunters about URL structure and its parsers.
Understanding the proper URL structure is important to every Bug bounty hunter. So lets go deep dive into the URL structure.
In WebSecurity, Mar 14, 2020